Cyber threats are a growing risk for businesses, as cybercriminals constantly find new ways to exploit vulnerabilities.
Staying aware of these threats is essential for companies looking to protect sensitive data, preserve customer trust, and ensure uninterrupted operations.
Tracking these threats is a proactive approach, allowing you to anticipate attacks before they cause harm.
Why Track Cyber Threats to Your Business
Tracking cyber threats provides several benefits. Here are some of them:
· Stay one step ahead: Spotting potential attacks early gives you the chance to stop them before they cause any harm.
· Protect sensitive data: Your business holds valuable information. Tracking threats helps keep it safe.
· Build customer trust: Showing you’re serious about security reassures your clients and builds loyalty.
· Save on costs: Prevention is a lot cheaper than cleaning up after an attack.
· Keep operations smooth: Staying vigilant means fewer disruptions and a steady flow of business.
· Stay compliant: Cyber regulations are strict. Monitoring threats keeps you on the right side of the law and helps you avoid penalties.
Gathering threat intelligence (TI) is one of the best ways to get a full picture of potential risks. This involves collecting and analyzing data on emerging cyber threats, providing information on the tactics, techniques, and procedures attackers use.
With TI, you can find out how potential threats are likely to unfold and which vulnerabilities they may exploit.
To simplify the threat intelligence collection process, you can use tools, such as ANY.RUN’s TI Lookup. This tool allows you to search for specific malware, monitor trends, and collect detailed information to understand the risks facing your business.
How to Collect Threat Intelligence on Cyber Threats
To show you how threat intelligence collection really works, let’s let’s examine a malware called XWorm, using ANY.RUN’s TI Lookup tool.
XWorm is a common threat, known for its ability to infiltrate systems across multiple industries. By using TI Lookup, you can gain insights into how XWorm operates, where it’s active, and what makes it a significant threat.
The easiest way to collect intel on this malware is by following these steps:
1. Run a search query
To start gathering intel, use TI Lookup’s extensive search capabilities, which offer over 40 customizable parameters. These parameters cover everything from malware sample details to OS, file, URL, registry, and module data, giving you a comprehensive view of each threat.
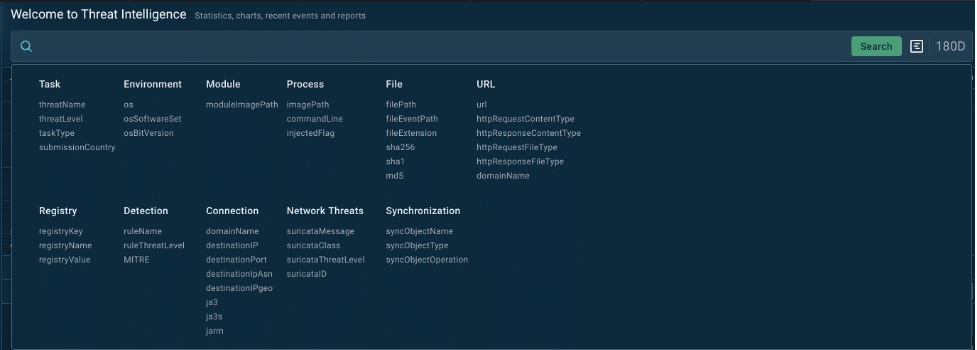
Search parameters in TI Lookup
For instance, to find specific data on XWorm, enter the query: threatName:”xworm” AND domainName:””. This search will generate a list of detailed threat intelligence focused on XWorm’s activity patterns.
The presented data is pulled from millions of malware analysis sessions in ANY.RUN’s sandbox.
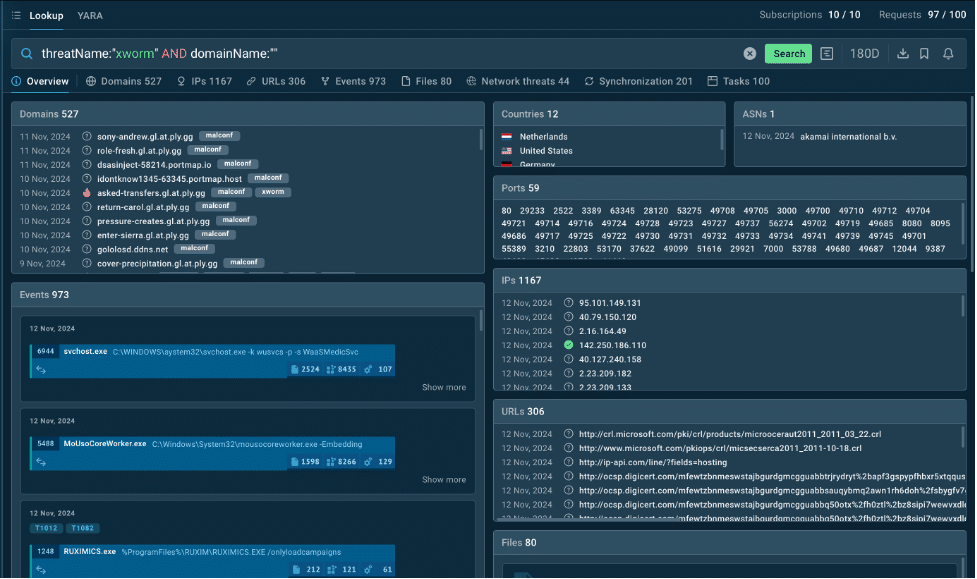
Search results in TI Lookup
2. Analyze the results
With TI Lookup, you can dive into a rich set of details about XWorm, offering a clearer picture of how this malware operates and where it poses the greatest risk. Here’s the kind of information you will uncover:
· Domains with Malconf: Look for entries marked with the malconf tag. These highlight domains where XWorm is actively configured. This tag reveals deeper configuration data that provides insight into how XWorm operates, from its intended targets to specific tactics.
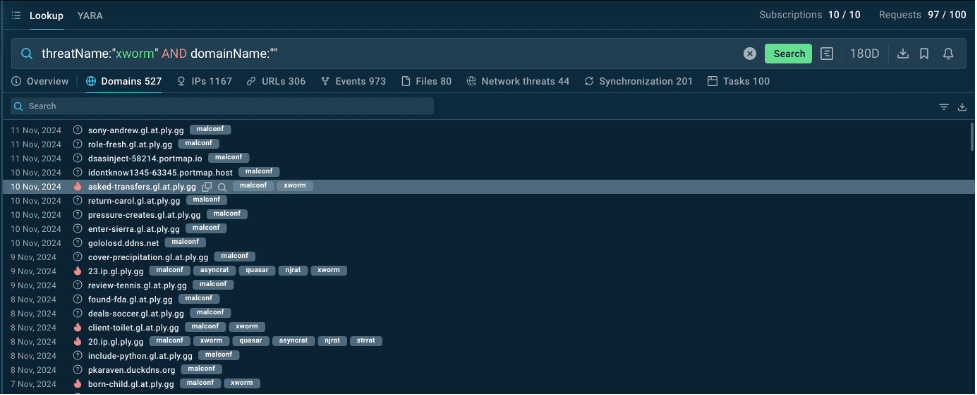
Domains with Malconf displayed by TI Lookup
· Countries of IP addresses: Identify the countries linked to the IP addresses used in XWorm attacks.

Find geolocation of XWorm’s IP addresses
· IPs and URLs: Find IP addresses and URLs associated with XWorm. These data points help pinpoint the origins of the threat and allow you to spot potentially malicious traffic sources or links. This knowledge is crucial for blocking risky domains or setting up alerts for similar activity.
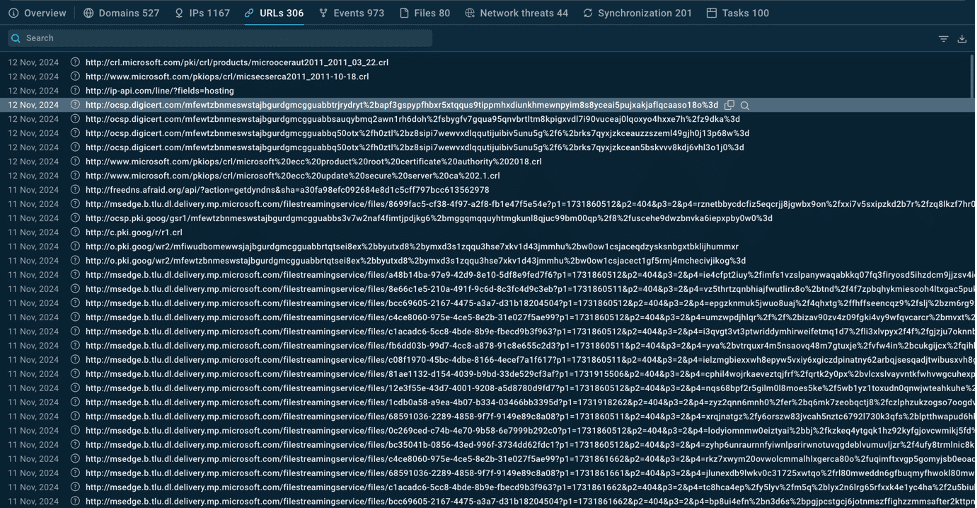
URLs related to XWorm malware inside TI Lookup
· Files and events: You’ll get a list of files and events tied to XWorm’s activity, giving you a closer look at its behavior. This information helps you understand the specific actions XWorm takes when it infects a system, so you know what to look for if it ever shows up in your network.
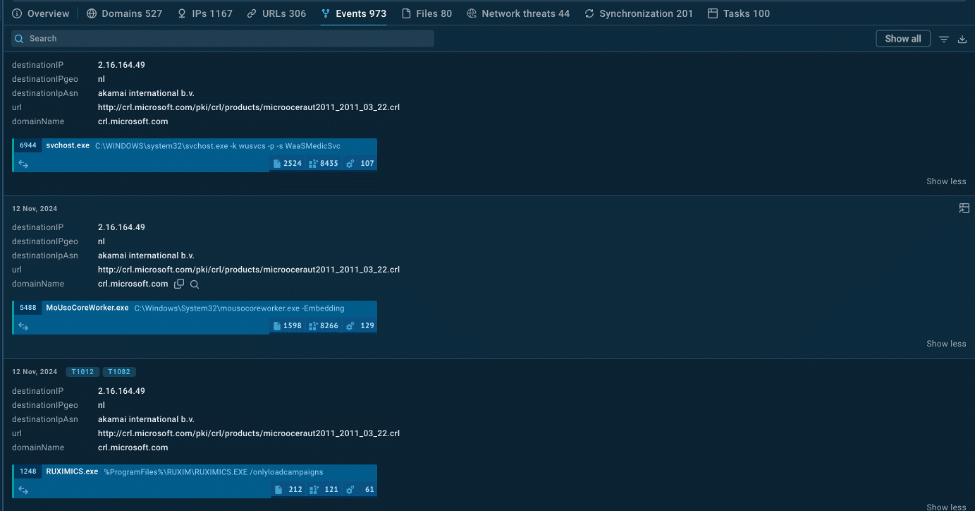
Events related to XWorm
· Network threats: TI Lookup also shows network-based indicators relevant to XWorm, helping you detect potential breaches from the network side. Recognizing these threats is key to strengthening your firewall settings and other network defenses.
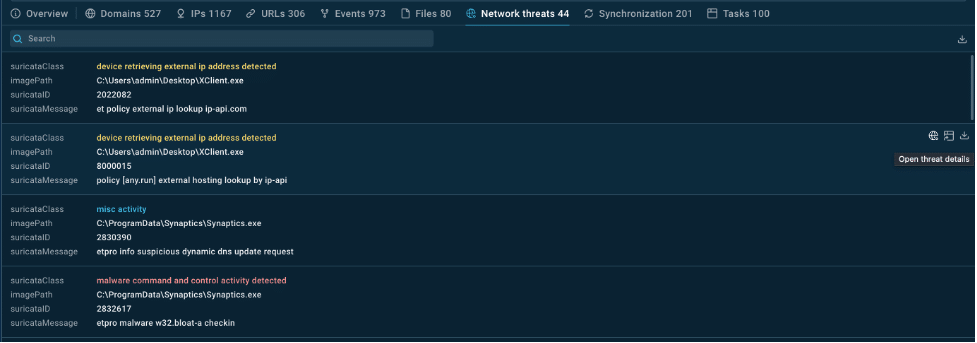
Network threats of XWorm pulled by TI Lookup
One of the most valuable features in TI Lookup is its access to real analysis sessions. You can browse sessions where other researchers have observed XWorm in action, all within a safe, isolated environment.
With a simple click, you can see how XWorm behaves step-by-step, allowing you to study its infection process, understand its evasive tactics, and learn from the experiences of others, all without putting your own systems at risk.
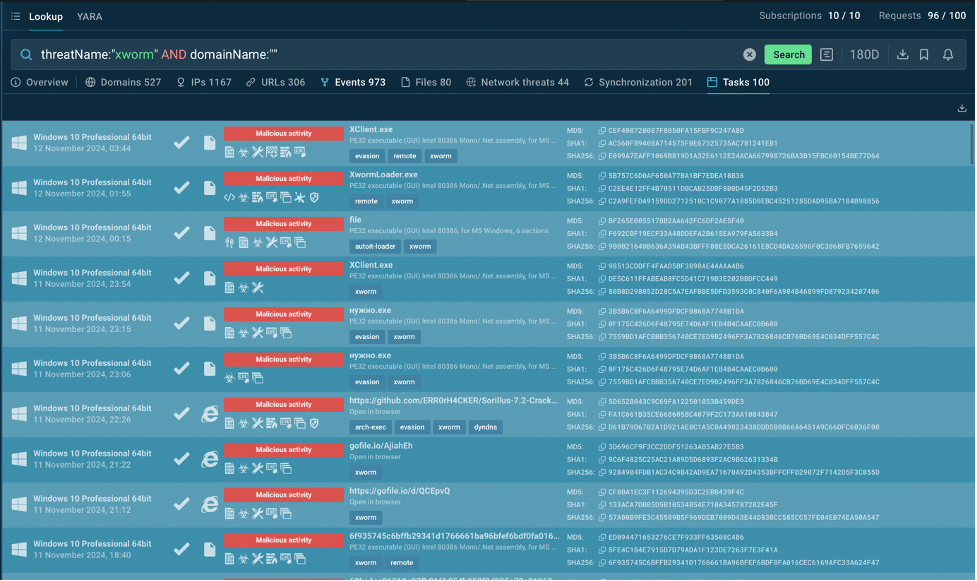
XWorm malware analysis sessions inside TI Lookup
Secure Your Business with Proactive Threat Intelligence
You don’t have to wait for threats to strike before taking action. ANY.RUN’s TI Lookup puts the control back in your hands, letting you dig deep into cyber threats like XWorm and act before they become real issues.
By understanding the patterns, origins, and behaviors of malware, you can build a solid line of defense that keeps your business safe.
With TI Lookup, you’ll have the insights to stay ahead, make informed decisions, and keep your systems secure.
Request a 14-day free trial of TI Lookup

