Malware poses a significant threat to businesses of all sizes, disrupting operations, stealing sensitive data, and leading to substantial financial losses. Despite this, many organizations remain unaware of their vulnerability.
A recent survey found that while 78% of companies believe they are well-protected against malware, nearly 50% have already been victims of such attacks.
As malware continues to evolve, it becomes more sophisticated, adapting to modern security measures and employing techniques to remain hidden. This constant evolution makes it increasingly challenging for businesses to detect and defend against these threats.
Types of Malware Impacting Businesses
Various types of malware can severely affect businesses, disrupting operations and compromising data security. Here are some of the most common types:
- Ransomware: Locks your files and demands payment for the decryption key.
- Spyware: Gathers information from your system without permission, often leading to data breaches.
- Trojans: Programs that appear safe but open backdoors for attackers to exploit.
- Botnets: A network of infected devices controlled by attackers to carry out large-scale cyber attacks like DDoS, spamming, or data theft.
To defend against these types of malware, it’s essential to analyze the files and emails your business receives. One effective solution is using an interactive sandbox like to safely examine suspicious files and websites, helping prevent potential harm before it happens.
| Sign up for free malware analysis on ANY.RUN |
Ransomware: Holding Data Hostage
Ransomware encrypts your company’s files and demands a ransom for decryption. This can lead to significant downtime, data loss, and potentially devastating financial repercussions. Commonly, attackers also threaten to leak sensitive data if the ransom isn’t paid.
LockBit is a great example of ransomware. It has been involved in high-profile attacks on major corporations. Companies attacked by LockBit face encrypted systems and data exfiltration.
Businesses can analyze ransomware threats by uploading suspicious files into the sandbox environment to observe its encryption methods and the ransom note in real time.
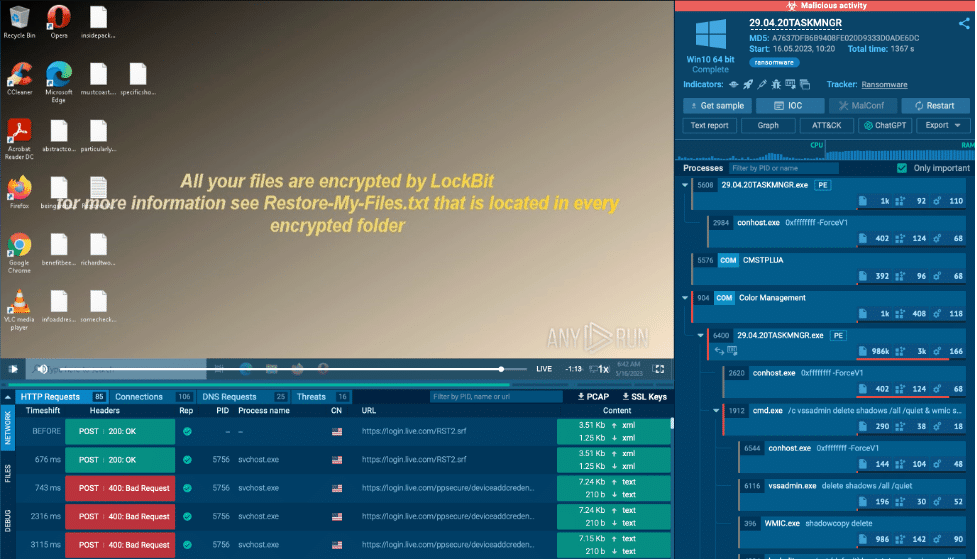
You can also analyze network traffic to detect communication with Command and Control (C2) servers. This helps determine the ransomware’s behavior and plan an effective response.
Trojan: Gaining Unauthorized Access
Trojans are disguised as legitimate software, enabling unauthorized access to your business’s systems. Once inside, attackers can remotely control your network, steal data, or deploy additional malware.
Emotet, originally a banking Trojan, is now widely used as a dropper for other malware, including ransomware and infostealers. It can quickly spread across networks, making it a versatile threat.
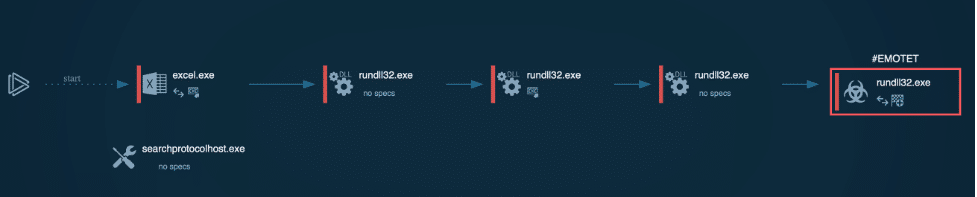
One of the trickiest aspects of this malware is that attackers sometimes use familiar names, such as colleagues, making the threat harder to detect. However, to minimize risk, it’s always advisable to check any received file inside the sandbox before opening it.
Once you upload a suspicious file into an interactive sandbox like ANY.RUN, you’ll be able to see all the details of its execution and prevent it from spreading within your company
Spyware: Monitoring and Collecting Data
Spyware secretly monitors user activity, collecting sensitive data such as login details, browsing habits, or intellectual property, and sends it back to the attacker. This can result in significant data breaches.
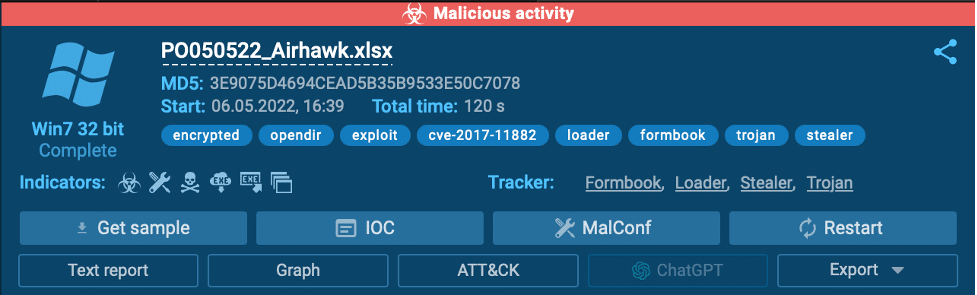
For example, FormBook is a widely recognized spyware that has been used in cyber espionage attacks. It is known for targeting credentials and harvesting sensitive information from its victims, often used in business or financial attacks.
You can easily observe malware behavior in ANY.RUN by searching public submissions, without downloading your own samples.
In this example, FormBook first connects to a CnC server. Next, it drops or overwrites a malicious file, disguised as a .png, and executes it. It then steals personal data, modifies autorun registry values, and loads a DLL from Mozilla Firefox.

Additionally, it creates files in the user directory, starts CMD.EXE for persistence, and begins process injection. Finally, the injected Firefox.exe logs keystrokes, steals clipboard data, and captures authentication info from browser sessions.
You can perform an in-depth analysis like this or simply upload your suspicious file and check the top right corner of the screen. If you see “malicious activity” highlighted in red, the file is dangerous. Below that, you’ll find indicators and potential threats listed for further analysis.
Botnets: Coordinating Large-Scale Cyber Attacks
A botnet is a network of compromised computers, often referred to as “zombies,” controlled remotely by attackers. These networks are used to carry out large-scale cyber attacks such as Distributed Denial of Service (DDoS), spamming, and credential theft. Each infected device communicates with a command and control (C2) server, allowing attackers to send instructions to the entire botnet simultaneously.
An example of a botnet-forming malware is Sality, which turns infected devices into part of a global network of compromised machines. These bots can be used to further spread malware, steal sensitive data, or conduct DDoS attacks.
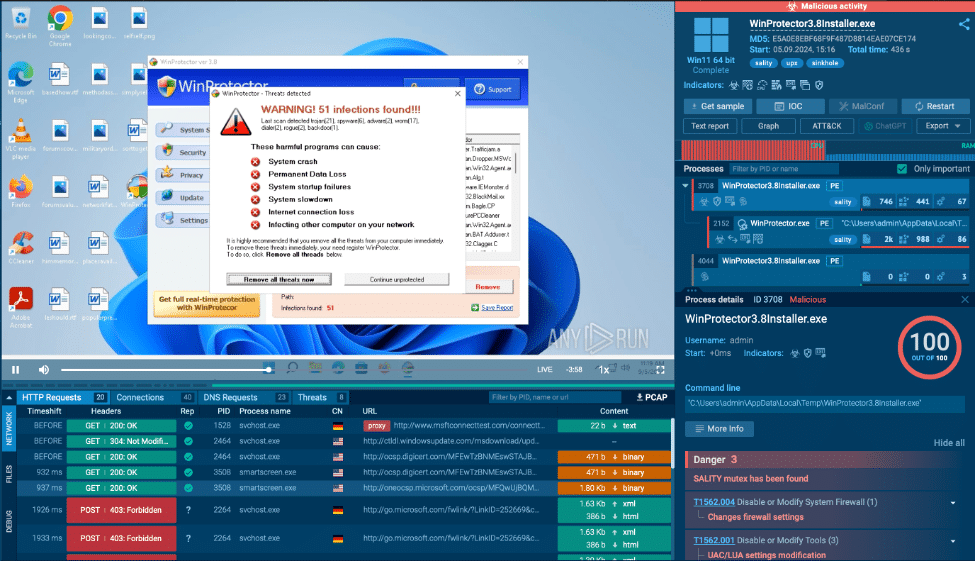
In the interactive sandbox, botnet behavior can be observed by watching how infected machines communicate with C2 servers. This insight helps security teams track how botnets form, understand their functions, and take steps to disrupt them.
Secure Your Business by Proactively Analyzing Malware
Malware can cause severe harm to businesses, leading to data breaches, financial losses, and operational disruptions, as highlighted above. However, companies can effectively defend against these threats by proactively analyzing malware behavior and thoroughly inspecting suspicious files and links that employees receive.
With ANY.RUN’s interactive sandbox, businesses can analyze malware in real-time, observe its behavior, and identify threats before they cause damage. By integrating tools like this into your security strategy, you can significantly reduce the risk of infection and stay one step ahead of cybercriminals.
Sign up for a 14-day free trial with ANY.RUN to start analyzing malware today!

